Cybersecurity for Small Businesses: A Comprehensive Guide
This post is also available in:
![]()
![]()
![]()
![]()
You hear a lot about data leaks and security hacks in the news. Most of the time, the ones you hear about are massive corporations or government agencies. You don’t often hear about the local hair salon or primary school having a data leak or a hacker attack. Despite the newsworthy prevalence of large scale cybersecurity breaches, small businesses can make attractive targets.
Smaller firms are subject to the same online security threats as any large corporation. However, the small or medium-sized company is made more vulnerable by the additional barriers to creating a secure online environment for their data.
Why small businesses make attractive targets
It’s a horrible thought, but when it comes to small businesses with online systems, they appear like ripe, low-hanging fruit for anyone willing to take advantage.
When you have a small business, you don’t usually have the resources to allocate a specialised team, or even a dedicated person, to the business of cybersecurity. This usually means that smaller firms have less stringent security protocols and fewer resources to search for leaks and threats. It’s no one’s fault, but it does make the smaller companies more vulnerable.
When anyone builds a business, they do it for their passion and expertise in that area. Unless you’re building a cybersecurity business, your area of expertise is not online security, and no one goes into business to spend hours of time way outside their specialism. This leads to people making mistakes, not taking their security measures seriously, and everyone knows that human error is one of the most significant security threats to any business.
Another element that makes smaller businesses more attractive to online threats is their connection to larger companies. With less robust systems and significant human data threats, smaller businesses can represent an easy access point to larger firms, with much more valuable data.
Another element that makes smaller businesses more attractive to online threats is their connection to larger companies. With less robust systems and significant human data threats, smaller businesses can represent an easy access point to larger firms, with much more valuable data.
A surprising factor in why small businesses are more susceptible to cyberattacks is that many don’t take cybersecurity as seriously as they should. There is a pervasive and erroneous belief that smaller firms aren’t as attractive as larger companies. Consequently, management isn’t as rigorous in implementing cybersecurity controls and policies.
What is at risk in a cybersecurity breach?
You keep a lot of data on the cloud and web-based servers. When your cybersecurity protocols aren’t robust, you risk any or all of that stored data. Moreover, you risk access to any internal systems linked to your web storage. Improper hardware deployment can also leave gaps in your security, exposing systems to vulnerabilities from misconfigured or outdated devices. Money, data, equipment, and your reputation are at grave risk of infiltration and disclosure.
- client information
- company banking details
- customer payment details
- product designs
- development plans
- processes
- pricing structure
Any of this data is a target for people wanting to sell the information or profit from your loss. It’s not merely your company details and stability at risk if your firm leaks this data from inadequate cybersecurity protocols. Your clients, partners, and even your suppliers could become targets through your company’s data leakage. Let’s not mention that you could be legally guilty if any data theft from your business fundamentally damaged another party.
It’s all very well knowing what data is at risk if you don’t keep on top of your internal and external cybersecurity protocols. Still, it’s work identifying what is at stake if your business falls victim to a cyberattack through poor preparation.
- Financial loss (via several avenues)
- through compromised banking details
- disruption of business
- liability claims against you
- Reputational Damage
- Losing clients due to leaking their data
- Bad reviews
- Legal repercussion
- violating client confidentiality
- noncompliance with data privacy and security laws (GDPR, HIPAA, etc.)
Most small businesses could not recover from these losses. Moreover, Small and mid-sized companies that have suffered one cyberattack are more likely to be targeted again. According to a study in 2012 by the National Cyber Security Alliance, 60% of small businesses go out of business within six months of a data breach.
The most common threats to small businesses
There are several common methods hackers and cybercriminals use to gain access to systems. They can cause more damag to small businesses as they would be to a massive entity like Facebook or Amazon. Unfortunately, they nearly always target the human element rather than trying to hack security software directly.
Phishing
Phishing attacks occur when the sender pretends to be a trusted contact, an internal colleague or, more often, someone in management. The masters of the phishing scam do their research. These online actors ensure that their emails look and sound like an email sent from the person they’re pretending to be, potentially down to having a single character difference in the email address. The sign off is the same, as is the tone, but they will ask you to download something, send sensitive information or send money.
Phishing emails have been commonplace for a long time, and many people have learned to ignore and report them. However, they are still significantly prevalent because their techniques and delivery have become much more sophisticated.
Malware
Malware is an overarching term used to describe various malicious code types that can infect your systems. Viruses or Trojans are designed to access machines and networks or steal and destroy data. Malware can find its way into your IT infrastructure by malicious website downloads, spam or phishing emails, or connecting to other affected devices.
Malware can be particularly hazardous to smaller businesses because it can cause damage to hardware as well as stealing data and taking control of networks. Most small companies can’t afford to spend thousands on replacing damaged hardware from an infected system.
Social Engineering
While social engineering doesn’t always lead to a malware infection, many phishing scams and malware have a social engineering element in their execution. This is where the research comes into play.
Cybercriminals that have mastered the art of social engineering cons know how to play on the duality of emotional engagement and risk.
Fear, Curiosity, Greed, Urgency, and helpfulness are all aspects of the social engineering plot.
Social engineers use your emotional responses to their malicious pop-ups, emails and infected websites to engage your fear of risk. It doesn’t matter whether that’s the risk of being unhelpful, missing out on a “great deal”, or the negative consequences of not downloading their “essential software” right now.
Sometimes it can be as simple as sending out a fun social media post designed to collect personal details. You’ve probably seen something like this on your feed.
Ransomware
Ransomeware does precisely what it says. It takes your company and client data and holds it up for ransom – all the while encrypting it so you couldn’t see it even if you had access. This threat is significantly more damaging to small businesses because they are least likely to have rigorous and frequent data backups. Consequently, these smaller firms are more likely to pay the ransom to retrieve access to their valuable data.
At the same time, ransomware is particularly harmful to the medical profession, where immediate access to patient records and computer systems is essential and can even be a case of life or death.
Insider threats
Whether intentionally or through security laxity, your internal employees and former staff members are the biggest threat to your company’s cybersecurity.
“People affect security outcomes more than technology, policies or processes.”
Gartner Magic Quadrant for Security Awareness Computer-Based Training, Joanna Huisman, 18 July 2019
It’s true; people are your biggest threat.
Cybersecurity best practices for small businesses
Use a firewall
A firewall is the first line of defence against cybercrime. While many companies use an external firewall to keep their data safe, others have begun using an internal firewall for an extra layer of protection against cyberattacks.
Document policies
Don’t let policy slide under the radar. Document the policies that you need in place to maintain cybersecurity. Willful neglect of employee security could be grounds for dismissal if your staff don’t keep the procedures you implement.
It’s not just about ensuring that your staff keep to the rules, but it also means you can derive a checklist of necessary actions required to keep your data secure.
Account for external devices
Many small businesses allow or even encourage their employees to use their own devices, such as mobile phones and tablets. This cuts down costs for the company, and the employee is held responsible for maintaining it. However, external devices can be a common entry point for malicious software to enter a system without even realising it.
Ensure that you have a BYOD (bring your own device) policy in place that dictates the necessary measures required for using their own devices. Some examples are: The device must lock within x minutes of being idle. The device must lock with a password known only to you.
Education for staff
Don’t just hand over the online security document and hope for the best. It’s vital that your staff understand your cybersecurity measures’ importance and why everyone is responsible. Invest some time training your staff on your security protocols and ensure you keep them up to date at least once a year.
Use Certified Cloud Technologies
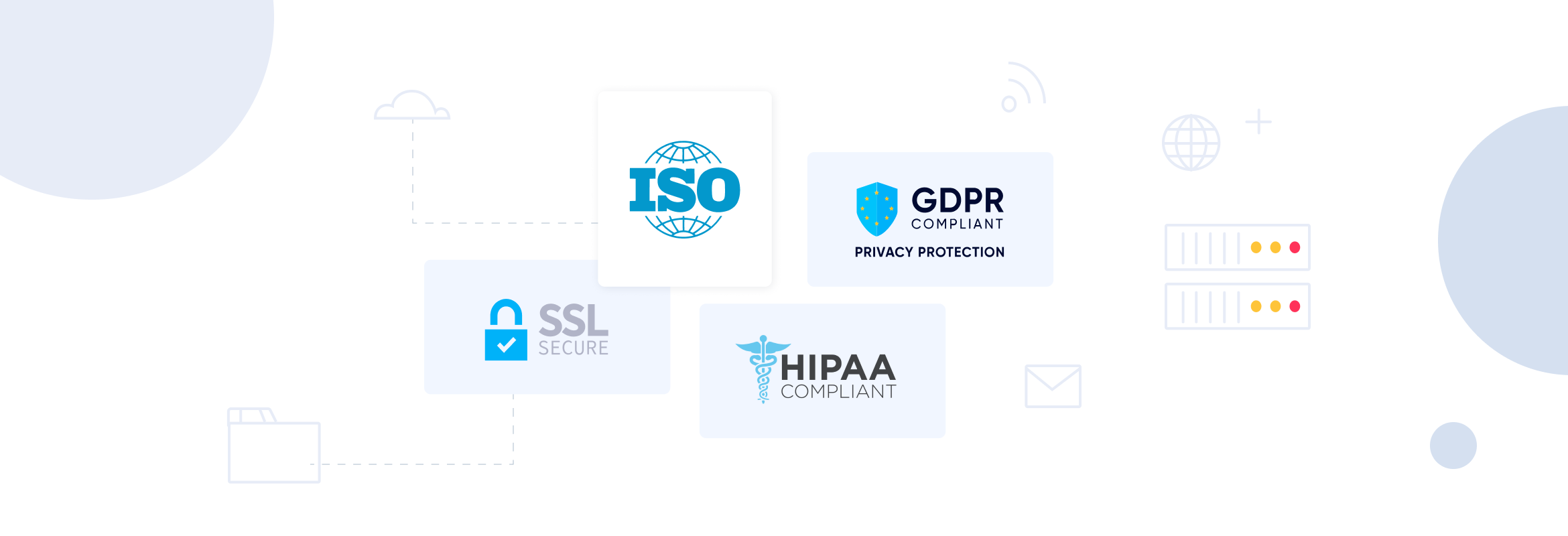
The firewall protects your infrastructure, but not of your business will be running on internal systems. Since the dawn of “as a service”, you might use a web-based scheduling system (SaaS) or Amazon web services (IaaS). Every web-based service you use should have certifications and policies that support your cybersecurity. Some examples are GDPR compliance, SSL(TLS), HIPAA, ISO certification, among many others. You might also choose to employ cloud monitoring tools to manage your cloud workflow, as well as an open source observability platform to measure the system’s current state.
Safe password policies
Creating a complex password to keep out brute force hackers and is also easy to remember is hard (at least for some). However, it is ultimately worth it. As part of your cybersecurity policies, you can implement password complexity requirements on most systems where you have ultimate control.
Regular and frequent back-ups
It’s an extra expense, but ensuring that your business and client data have regular and off-site backups is crucial. Not only to avoid the complete freezing of your business if someone attacks you will ransomware but also in case of other disasters that might occur.
It’s cheaper than having to halt your business or pay a ransom to get your data back.
Software protection
In the protection of your hardware system from malware, it’s best to take a proactive approach. While no anti-malware or anti-spyware package is perfect (because hackers develop just as fast as the protective programmers), using them is another layer of protection against malicious software infiltration.
Most of the time, the security software will identify the source of the malicious code, which will allow you to identify and block that source from future access to your system.
Multifactor identification and authorisation
Despite the developments in protective measures, single password access to secure systems is not a good idea. The easiest way to ensure secure password access is by adding an extra factor to the sign-in process. The easiest and cost-free way to do it is to use Google Authenticator 2-factor authentication, which will send a code to an external device for extra sign-in security.
There are alternative methods available to create additional security layers. Some require biometric input, such as fingerprints or facial recognition, while others are external key fobs, like a Yubikey.
Free resources for cybersecurity in your region
You might think that cybersecurity protocols would be roughly the same worldwide; the internet is everywhere. However, several agencies can help you design and implement a practical and functional system for cybersecurity controls for your small business. If they are specific to your region or country, the easier it will be to work with them within regional guidelines and laws.
- European Union countries
- USA
- Australia
- UK
Small business cybersecurity: In Summary
When you run a small or mid-sized company, you face obstacles to your cybersecurity maintenance that large corporations don’t have. You don’t have the whole security teams dedicated to ensuring your data safety.
You don’t have the time to dedicate hours to cybersecurity procedures and processes. These are significant barriers to creating a safe environment for business and client data.
There are resources available from local government agencies to help small businesses keep their data safe because a vast proportion of cyberattacks are targeted at small firms. Given that small businesses make up a large proportion of the economic input, it’s in the government’s best interests to keep them safe.
It doesn’t have to be expensive to implement best practices, but it won’t be free. There’s no way to ensure the most robust protection without any financial investment; however, the majority of the best practices cost nothing but time and effort.
The best protection is to train your staff about the dangers of cyberattacks and how to avoid them. People are the most significant threat because they have all the erratic emotions and reactions that are unpredictable. Training them to identify their triggers and spot false emails and other scams will be the most potent action to mitigate cybersecurity risks.

Comments
1 comments